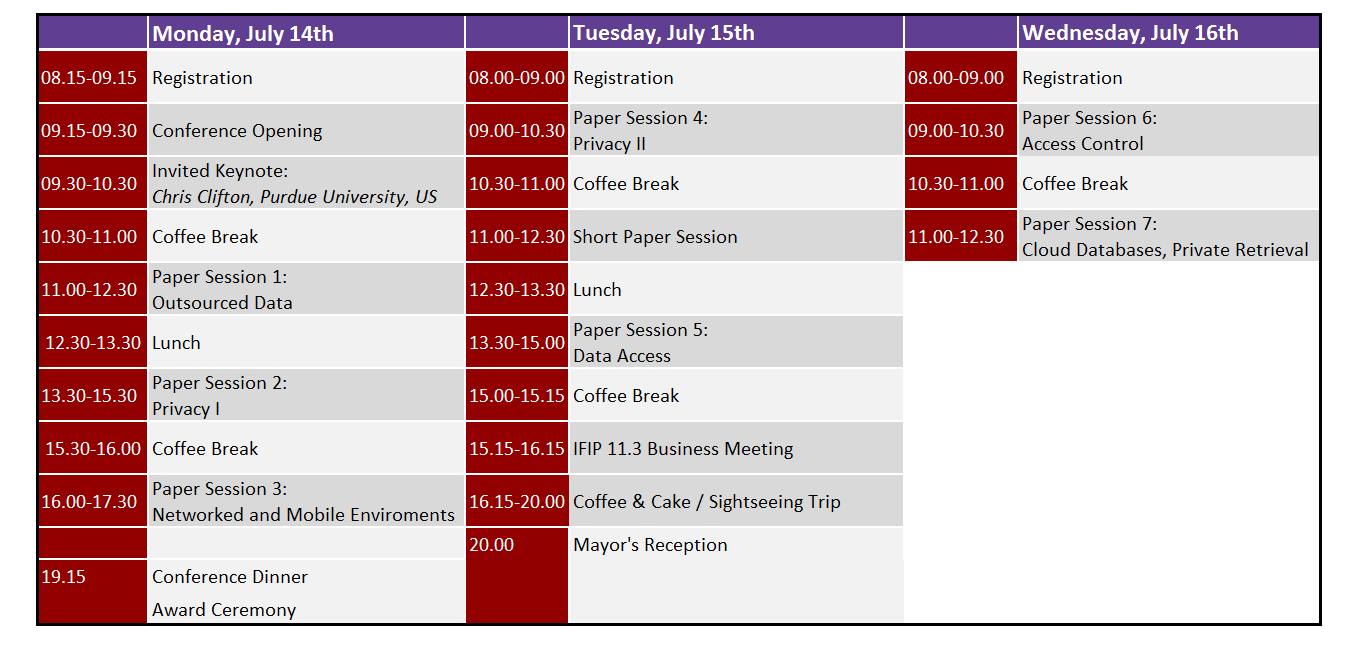
Monday, July 14th, 2014
08:15 – 09:15 Registration
09:15 – 09:30 Conference Opening
09:30 – 10:30 Invited Keynote I
Session Chair: Vijay Atluri
Privacy without encrypting – Protect your data and use it too (Abstract)
Christopher W. Clifton, Purdue University, US
11:00 – 12:30 Paper session 1: Outsourced Data
Session Chair: Edgar Weippl
- Integrity Assurance for Outsourced Databases without DBMS Modification
Wei Wei and Ting Yu (North Carolina State University) - Specification and Deployment of Integrated Security Policies for Outsourced Data
Anis Bkakria, Frédéric Cuppens, Nora Cuppens-Boulahia and David Gross-Amblard (Télécom Bretagne, IRISA) - Optimizing Integrity Checks for Join Queries in the Cloud >>BEST PAPER Award<<
Sabrina De Capitani Di Vimercati, Sara Foresti, Sushil Jajodia, Stefano Paraboschi and Pierangela Samarati (Università degli Studi di Milano, George Mason University, Università di Bergamo)
12:30 – 13:30 Lunch
13:30 – 15:30 Paper session 2: Privacy I
Session Chair: Gail-Joon Ahn
- Privacy-Enhancing Proxy Signatures from Non-Interactive Anonymous Credentials
David Derler, Christian Hanser and Daniel Slamanig (Graz University of Technology (TUG)) - Privacy-Preserving Multiple Keyword Search on Outsourced Data in the Clouds
Tarik Moataz, Benjamin Justus, Indrakshi Ray, Nora Cuppens-Boulahia, Frédéric Cuppens and Indrajit Ray (Colorado State University, Télécom Bretagne) - Secure and Privacy-Preserving Querying of Personal Health Records in the Cloud Samira Barouti, Feras Aljumah, Dima Alhadidi and Mourad Debbabi (Concordia University)
- Data Leakage Quantification >>BEST STUDENT PAPER Award<<
Sokratis Vavilis, Milan Petkovic and Nicola Zannone (Eindhoven University of Technology, Philips Research Europe)
16:00 – 17:30 Paper session 3: Networked and Mobile Environments
Session Chair: Sabrina De Capitani di Vimercati
- Toward Software Diversity in Heterogeneous Networked Systems
Chu Huang, Sencun Zhu and Robert Erbacher (Penn State University, U.S. Army Research Laboratory (ARL)) - FSquaDRA: Fast Detection of Repackaged Applications
Yury Zhauniarovich, Olga Gadyatskaya, Bruno Crispo, Francesco La Spina and Ermanno Moser (University of Trento) - `Who, When, and Where?‘ Location Proof Assertion for Mobile Devices
Rasib Khan, Shams Zawoad, Md Munirul Haque and Ragib Hasan (University of Alabama at Birmingham)
19:15 Conference Dinner, Award Ceremony
Tuesday, July 15th, 2014
09:00 – 10:30 Paper session 4: Privacy II
Session Chair: Sokratis Vavilis
- Design Patterns for Multiple Stakeholders in Social Computing
Pooya Mehregan and Philip W. L. Fong (University of Calgary) - Collaboratively Solving the Traveling Salesman Problem with Limited Disclosure
Yuan Hong, Jaideep Vaidya, Haibing Lu and Lingyu Wang (SUNY-Albany, Rutgers University, Santa Clara University, Concordia University) - ELITE: zEro Links Identity managemenT systEm
Tarik Moataz, Nora Cuppens-Boulahia, Frédéric Cuppens, Indrajit Ray and Indrakshi Ray (Colorado State University, Télécom Bretagne)
11:00 – 12:30 Short paper session
Session Chair: Ravi Sandhu
- LPM: Layered Policy Management for Software-Defined Networks
Wonkyu Han, Hongxin Hu and Gail-Joon Ahn (Arizona State University, Delaware State University) - On Minimizing the Size of Encrypted Databases
Giovanni Di Crescenzo and David Shallcross (Applied Communication Sciences) - Efficient and Enhanced Solutions for Content Sharing in DRM Systems
Michal Davidson, Ehud Gudes and Tamir Tassa (The Open University, Ben-Gurion University) - A Scalable and Efficient Privacy Preserving Global Itemset Support Approximation using Bloom Filters
Vikas Ashok and Ravi Mukkamala (SUNY Stony Brook, Old Dominion University)
12:30 – 13:30 Lunch
13:30 – 15:00 Paper session 5: Data Access
Session Chair: Stefano Paraboschi
- Dynamic Workflow Adjustment With Security Constraints
Haibing Lu, Yuan Hong, Yanjiang Yang, Yi Fang and Lian Duan (Santa Clara University, University at Albany, I2R Singapore, New Jersey Institute of Technology) - Consistent Query Plan Generation in Secure Cooperative Data Access
Meixing Le, Krishna Kant and Sushil Jajodia (George Mason University) - Hunting the Unknown – White-Box Database Leakage Detection
Elisa Costante, Jerry Den Hartog, Milan Petkovic, Etalle Sandro and Mykola Pechenizkiy (Eindhoven University of Technology, Philips Research Europe)
15:15 – 16:15 IFIP 11.3 Business Meeting
16:15 Departure Coffee & Cake / Sightseeing Tour
20:00 Mayor’s Reception
Wednesday, July 16th, 2014
09:00 – 10:30 Paper session 6: Access Control
Session Chair: Haibing Lu
- Incremental Analysis of Evolving Administrative Role Based Access Control Policies
Silvio Ranise and Anh Truong (FBK-Irst, Fondazione Bruno Kessler, Trento) - Mining Attribute-Based Access Control Policies from Logs
Zhongyuan Xu and Scott Stoller (Stony Brook University) - Attribute-aware Relationship-based Access Control for Online Social Networks
Yuan Cheng, Jaehong Park and Ravi Sandhu (University of Texas at San Antonio)
11:00 – 12:30 Paper session 7: Cloud Databases, Private Retrieval
Session Chair: Ehud Gudes
- Randomly Partitioned Encryption for Cloud Databases
Tahmineh Sanamrad, Lucas Braun, Donald Kossmann and Ramarathnam Venkatesan (ETH Zurich, Microsoft Research) - Towards Secure Cloud Database with Fine-Grained Access Control
Michael Solomon, Vaidy Sunderam and Li Xiong (Emory University) - Practical Private Information Retrieval from a Time-Varying, Multi-Attribute, and Multiple-Occurrence Database
Giovanni Di Crescenzo , Debra Cook, Allen McIntosh and Euthimios Panagos (Applied Communication Sciences)